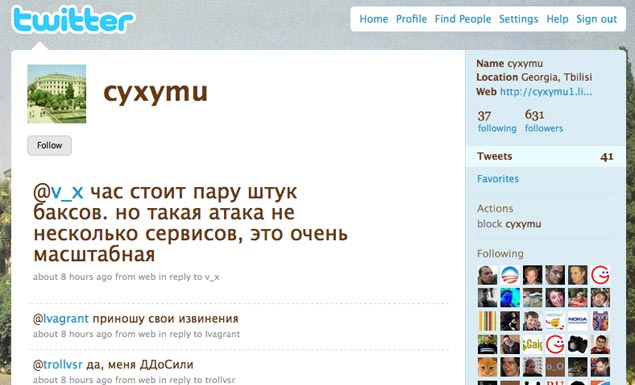
Tech, World: To silence ONE GUY, Russia had to take down Twitter
- The lack of logic and high level of selfishness here (on Russia’s part) is atrocious. Russian authorities tried to silence Cyxymu, a.k.a. “George,” for his stance on the Georgia conflict. (The timing was political.) But instead, Russia tried to shut down every major social network, causing the guy they wanted to silence to have an even bigger voice. Genius, Russia. Just genius.source